I did work on a new approach where we do the signature verification on a blinded key, such that we can move the heavy EC operations outside the ZK environment (see the discussion here: (EDITED) following README example - slower proving time? · Issue #10 · halseth/output-zero · GitHub).
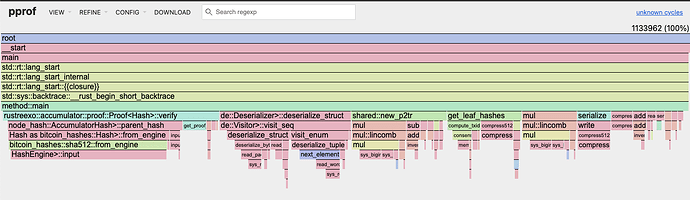
This results in the SHA-512 hashing in verifying the utreexo proof dominating the runtime:
@Davidson How easy is it to either
- Switch to using the
poseidon2hash function for this, OR use the Risc0 precompile for SHA-512 (it looks like rustreexo is using thebitcoin_hashes::Sha512implementation).
I see that this is made possible in the latest rustreexo release ![]()