Btcd prior to version v0.24.0 does not correctly implement the consensus rules outlined in BIP 68 and BIP 112, making it susceptible to consensus failures. Btcd users are advised to upgrade to version v0.24.0 or above.
Details
BIP 68 & 112 describe two soft-forks that introduced relative time locks to Bitcoin transactions (necessary for e.g. Hash Time Locked Contracts). The rules outlined in the BIPs are only active for transactions with version 2 or higher.
While both Bitcoin Core and btcd store the transaction version as a signed 32-bit integer, in the context of BIP 68 & 112 it is supposed to be treated as unsigned (otherwise half the range of the version would not support BIP 68 & 112). Btcd however, used the signed transaction version in both the BIP 68 and BIP 112 logic without a prior cast to uint32. As consequence, transactions with negative versions are incorrectly treated as not enforcing the BIP 68 rules or incorrectly rejected for use of OP_CHECKSEQUENCEVERIFY (BIP 112).
Impact
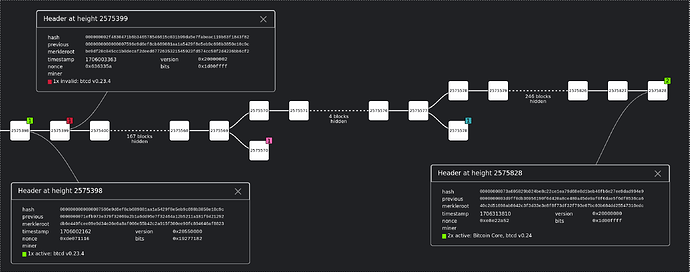
If triggered, these bugs can result in btcd nodes not accepting a block that Bitcoin Core nodes would accept (or vice versa), resulting in a chain split. Chain splits can lead to e.g.:
- Lightning Nodes using btcd as their chain backend are at risk of losing funds due to not receiving updates for the canonical chain.
- An attacker could trigger a split and then mine on the “btcd chain” (likely without competition from other miners) to trick btcd users into accepting payments that can’t occur on the canonical chain.
- Miners that use btcd are at risk of mining on top of an invalid chain, wasting their resources.
Transactions with negative versions are non-standard but as the recent past has shown, that would not represent a significant hurdle for an attacker.
Credits
Thanks to the btcd project for awarding me with a bug bounty reward of 0.023 BTC and thanks to Guido Vranken for suggesting differential fuzzing of btcd’s and Bitcoin Core’s script interpreter to me.
Timeline
- 22-05-2023 - Initial disclosure to Lightning Labs
- 21-06-2023 - Fixed merged into btcd (multi: Run gofmt on the entire repository by kcalvinalvin · Pull Request #1981 · btcsuite/btcd · GitHub)
- 31-12-2023 - btcd v0.24.0 released
- 22-01-2024 - Public disclosure
Support security-focused Bitcoin research and development by donating to Brink.